Cyber Security Resources Hub
Welcome to our Cyber Security Resources Hub!
At Rose Computer Technology Services, we understand the importance of staying ahead in the ever-evolving landscape of cyber threats. That’s why we’ve curated a comprehensive collection of valuable resources to empower you in protecting your business from potential cyber attacks.
Explore our downloadable materials and PDFs, known as “leave behinds,” designed to provide actionable insights and practical guidance:
Defending the Digital Realm – A Comprehensive Guide to Cybersecurity Risk Assessment: Gain a deep understanding of cybersecurity risk assessment and learn how to effectively defend your digital assets.

Defending the Digital Realm - A Comprehensive Guide to Cybersecurity Risk Assessment
Implementing Cybersecurity Risk Assessment (CSRA) Is Essential to Safeguard Your Company’s Assets and Protect Sensitive Information: Explore the importance of implementing CSRA practices to mitigate risks and protect your company’s valuable assets and sensitive information.

Implementing Cybersecurity Risk Assessment (CSRA) Is Essential to Safeguard Your Company's Assets and Protect Sensitive Information
15 Ways to Protect Your Business from a Cyber Attack: Discover key strategies and best practices to safeguard your business against cyber threats.

15 Ways to Protect Your Business from a Cyber Attack
Is Your Car Dealership in Compliance with the Recently Released Federal Trade Commission Safeguards Update?: Stay informed about the latest regulations and ensure your dealership meets compliance standards set by the FTC.

Help Protect Your Business So You Can Focus on What Matters Most
Help Protect Your Business So You Can Focus on What Matters Most: Learn why prioritizing cybersecurity is crucial for the longevity and success of your business, allowing you to focus on your core objectives.
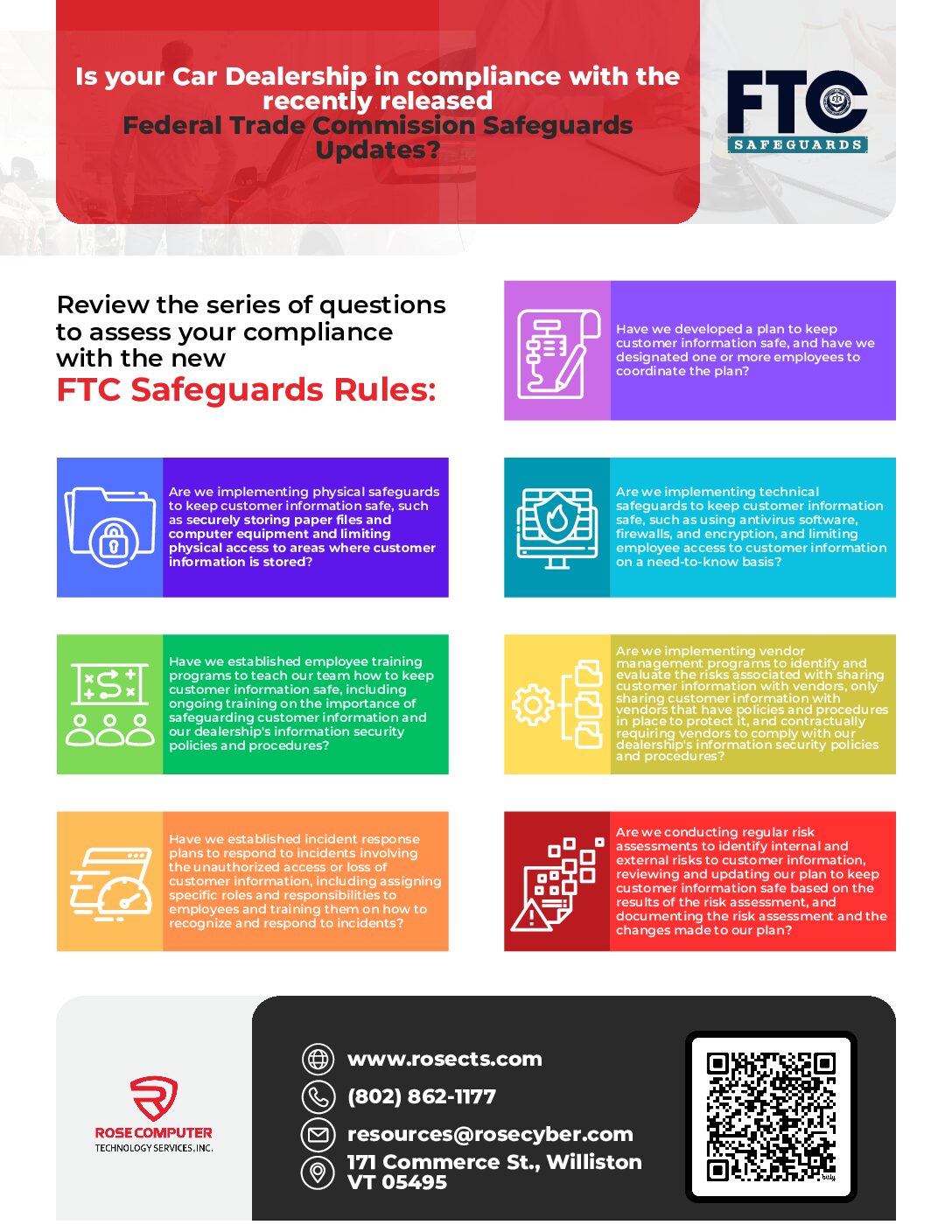
Is Your Car Dealership in Compliance with the Recently Released Federal Trade Commission Safeguards Update?
The 4 Stages of Cyber Risk Management: Effective cyber risk management is vital for protecting your business from potential threats. Our checklist outlines the four key stages of cyber risk management, providing actionable steps to identify, assess, mitigate, and monitor risks. Ensure your business is well-prepared to handle any cyber threat that comes its way.
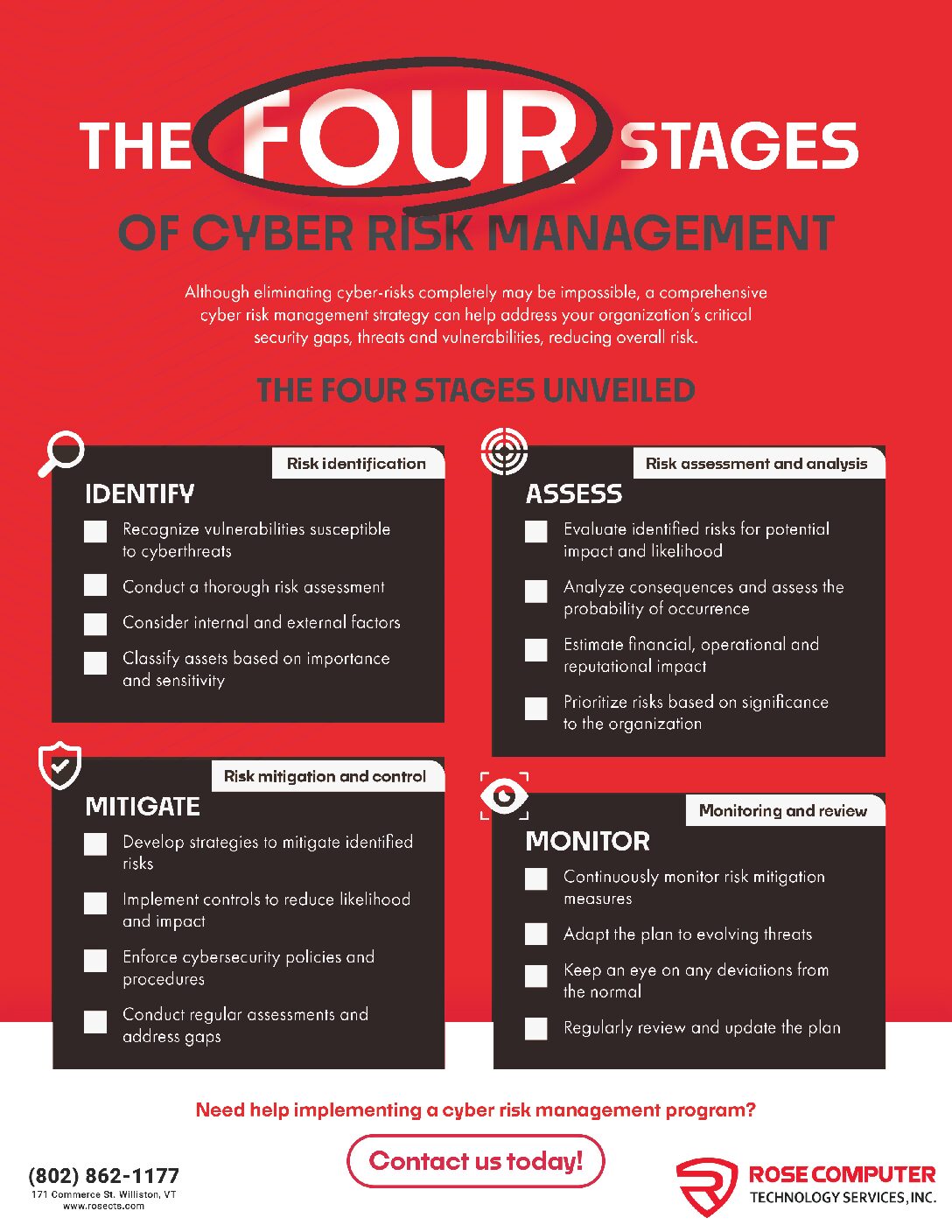
The 4 Stages of Cyber Risk Management
How Digital Transformation Drives Business Success: Uncover the direct link between digital transformation and business success. This resource explores how integrating digital technologies can enhance operational efficiency, customer experience, and overall business performance. Learn why adopting a digital-first approach is crucial for sustained growth and competitiveness.

How Digital Transformation Drives Business Success
6 Crucial Steps to Achieve Digital Transformation: Digital transformation is more than a buzzword; it’s a strategic necessity. Discover the six essential steps to successfully transition your business into the digital age. This guide will help you streamline processes, leverage new technologies, and stay ahead in a rapidly evolving market.

6 Crucial Steps to Achieve Digital Transformation
8 Steps to Protect Your Business from Cyber Threats: Follow a step-by-step guide outlining essential measures to fortify your business’s defenses against cyber threats.

8 Steps to Protect Your Business From Cyber Threats
Cyber Security Planning for 2025 – Everything You Need to Consider: Anticipate future challenges and plan ahead with our comprehensive guide to cybersecurity planning for the year 2025.

Cyber Security Planning for 2025: Everything you Need to Consider
Whether you’re a small business owner, a car dealership manager, or a corporate executive, our resources are tailored to equip you with the knowledge and tools needed to navigate the complexities of cybersecurity with confidence.
Download your desired materials today and take proactive steps towards enhancing your cyber resilience. At Rose Computer Technology Services, we’re committed to safeguarding your digital future.
Stay secure, stay empowered.

